Hackerspace Network Planning
| This article is a Draft. Information within may be incomplete; use at your own risk. |
Contents
Hackerspace Network Planning
This page serves as a place for ideas for the Hackerspace computer network; and how it plans to be grown out as we gain resources or members.
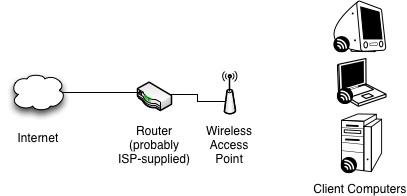
Minimal Network Layout
In a very, very minimal network layout, we can simply use whatever off-the-shelf router (very possibly the one supplied by our ISP, or someone's WRT54GL) to get internet access into the hackerspace.
This is plenty for an initial buildout, cheap to set up, quick to deploy; but a little limiting, as well as full of single points of failure. Definitely enough to get us access during our initial buildout.
Actual Network Layout
As we grow, we will want some actual segregation of traffic, the ability to put firewalls in place, some redundancy, and the ability to issue subnets to hackerspace projects as needed. As well, I'd like to get a colocation network in place for permanent or semi-permanent projects that may be hosted on the hackerspace network and/or exposed to the internet.
In addition, being able to sublet our traffic out to other sub-tennants, if necessary, would be a useful addition. For that, we'd also want some form of rate-limiting on both networks (to offer some reliable level of service to both the Hackerspace's network clients, and our sublet clients).
Proposed Subnet Division
TBD
Proposed physical network layout
TBD
Proposed features
TBD
Proposed/Necessary Network Applications and Services
- LDAP
- DNS
- DHCP
- Shared file server/homepage store
- Squid proxy (if we aren't likely to have a wide pipe, this is probably a good idea)
- Backup server?
- Mirror of popular linux distribution repositories?
- IDS/other security features?
- VoIP server?
Physical network considerations
- How many drops do we need? Where?
- Do we expect high amounts of EMF?
- Do we care about restricting access to the wireless network?
- Should we consider drops to points of entry (for security checkpoints, display dashboards, or more?)
- What policies should we have in place if someone wants to expand the location of network drops?